Basic iptables
Introduction
Kubernetes kube-proxy provides the important role to work with Service resource. kube-proxy will create and define iptables rules to manipulate the network traffic for the service resource. iptables is a Linux firewall.
In this article, we will introduce very basic iptables concepts: tables, chains and targets. Tables are files are join similar actions. There are several build-in tables. Chains are the set of rules. Rules are statements about what to do with the network package. Each rule contain one target. Targets are a decision or action of what to do. One target can point to a chain.
iptables -t nat -L -v
...
Chain PREROUTING (policy ACCEPT 415 packets, 33761 bytes)
pkts bytes target prot opt in out source destination
5392 456K KUBE-SERVICES all -- any any anywhere anywhere /* kubernetes service portals */
10 624 DOCKER all -- any any anywhere anywhere ADDRTYPE match dst-type LOCAL
Chain DOCKER (2 references)
pkts bytes target prot opt in out source destination
0 0 RETURN all -- docker0 any anywhere anywhere
...
iptables Targets
The most targets are ACCEPT, DROP, REJECT. However, there are many other targets which can be used in various cases.
- ACCEPT: this rule accepts the packets to come through the iptables firewall.
- CLASSIFY: it can be used to classify packets in such a way that can be used by a couple of different qdiscs (Queue Disciplines).
- DSCP: it is able to set any DSCP value inside a TCP packet, which is a way of telling routers the priority of the packet in question.
- DNAT: it is used to do Destination Network Address Translation, which means that it is used to rewrite the Destination IP address of a packet.
- DROP: it drops the package which is not matched against any further chain.
- QUEUE: it will pass the packet to the userspace.
- ECN: it can be used to reset the ECN bits from the IPv4 header, or to put it correctly, reset them to 0 at least.
- RETURN: it sends the packet back to the originating chain so you can match it against other rules.
- REJECT: it rejects a packet and sends an error to the connecting device.
- LOG: it is specially designed for logging detailed information about packets.
- MARK: it is used to set Netfilter mark values that are associated with specific packets.
- MASQUERADE: it is used basically the same as the SNAT target, but it does not require any –to-source option.
- MIRROR: it is an experimental and demonstration target only, and you are warned against using it, since it may result in really bad loops hence, among other things, resulting in serious Denial of Service. [1]
- NETMAP: it is a new implementation of the SNAT and DNAT targets where the host part of the IP address isn’t changed.
- REDIRECT: it is used to redirect packets and streams to the machine itself.
- SAME: it works almost in the same fashion as the SNAT target, but it still differs.
- SNAT: it is used to do Source Network Address Translation, which means that this target will rewrite the Source IP address in the IP header of the packet.
- TCPMSS: it can be used to alter the MSS (Maximum Segment Size) value of TCP SYN packets that the firewall sees.
- TOS: it is used to set the Type of Service field within the IP header.
- TTL: it is used to modify the Time To Live field in the IP header. One useful application of this is to change all Time To Live values to the same value on all outgoing packets.
- ULOG target is used to provide user-space logging of matching packets.
We also provide some examples to illustrate how iptables works for each service.
MARK example
Chain KUBE-MARK-MASQ (45 references)
pkts bytes target prot opt in out source destination
6614 621K MARK all -- any any anywhere anywhere MARK or 0x4000
Chain KUBE-POSTROUTING (1 references)
pkts bytes target prot opt in out source destination
6468 612K MASQUERADE all -- any any anywhere anywhere /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE
The MASQUERADE target is always put into POSTROUTING chain to hide the source IP address. (SNAT)
Chain POSTROUTING (policy ACCEPT 5000 packets, 324K bytes)
pkts bytes target prot opt in out source destination
43268 3538K KUBE-POSTROUTING all -- any any anywhere anywhere /* kubernetes postrouting rules */
DNAT
DNAT is used to do Destination Network Address Translation, which means that it is used to rewrite the Destination IP address of a packet. One concept in firewall is virtual IP (VIP), which exposes internal service IP address to external network.
Chain KUBE-SEP-MOMZQBEI6PSIABOH (1 references)
pkts bytes target prot opt in out source destination
0 0 KUBE-MARK-MASQ all -- any any ip-172-28-5-61.ec2.internal anywhere
0 0 DNAT tcp -- any any anywhere anywhere tcp to:172.28.5.61:53
iptables Tables
Generally, iptables contains five build-in tables:
- Filter: Filter table has three default chains: INPUT, OUTPUT and FORWARD
- NAT: NAT table has tree default chains: PREROUTING, OUTPUT and POSTROUTING.
- Mangle: Mangle table adjusts the IP header properties of packets. Mangle table is for specialized packet alteration. This alters QOS bits in the TCP header. Mangle table has the following built-in chains.
- Raw: Raw table is for configuration exemptions. Raw table has the following built-in chains: PREROUTING and OUTPUT.
- Security table
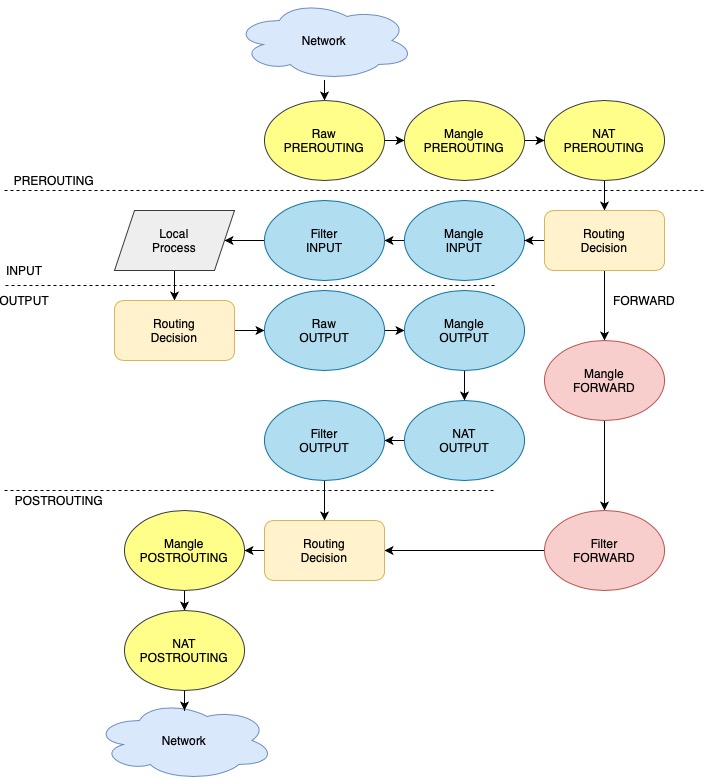
When a network packet is coming in, iptables finds the appropriate table, then runs it through the chain of rules until it finds a match.
The following diagram shows how iptables traverse each tables and chains.